This is often the first thing that is said (after the introductions)
when I go to companies to talk about GDPR and frequently I don’t know
what to say.
Let’s start with data protection. It all started about 16 years ago
when I was put in charge of data protection for a charity I was working
for. I have to admit it was like the blind leading the blind. I didn’t
have a clue and data protection seemed to be contradictory and
confusing. Luckily I got some training and then a few years later I took
the BCS exams for Data Protection Officers. This was enlightening, it
all started to click into place. I kept up to date with the new things
and because I only worked for the charity part time, word spread that I
would help other organisations with their data protection practices.
Work came in by referral. Then GDPR appeared and there was a whole lot
more to learn and decipher and more organisations needing support and
advice.
In addition to my data protection qualification, I have been an
internal auditor for nearly 30 years, so I know how to look for
information, ask people how they work and create effective process
improvements. I’m also a qualified Institute of Leadership and
Management Level 5 Coach and Mentor, a member of the Association of
Accounting Technicians and earlier this year completed the Institute of
Risk Management Exams.
So how do I work? First up, I don’t claim to be an expert on GDPR, at
this time nobody is, there are too many unknowns about how the
legislation is going to be interpreted but I do have 15 years experience
actually working with businesses to support their data protection
practices. I don’t believe in making things onerous, if there is a
straightforward way of doing things I will choose that, why
overcomplicate it. I don’t use the jargon or recite the articles or
recitals, you’ll get the plain English version from me. I also believe
that data protection compliance shouldn’t be an add on but should be
part of the way you do business, it should be embedded into your
business practices. I believe that every member of staff should have
basic understanding of the Data Protection Act and GDPR, it shouldn’t be
one persons responsibility. Its too difficult to make one person
responsible for a whole organisations data protection practices and it
means frequently that people negate responsibility because it is
“someone else’s job”.
My aim is to create the right solution of each business I work with,
it’s not about you fitting to the legislation but how the legislation
fits your organisation, your business strategy, your aspirations.
With GDPR as the new “Y2k” for consultants and every Tom, Dick and
Harriet jumping on the bandwagon, there is lots of choice for
businesses. Many people have read the legislation and know the law, but I
know that and how to implement it into a variety of businesses.
Companies work with me because I have a pragmatic approach, can
implement cost effective solutions, manage the changes required and I
have experience in a variety of industries.
If that sounds like someone you want to work with, then I would be very happy to talk GDPR with you.
Showing posts with label Data Protection. Show all posts
Showing posts with label Data Protection. Show all posts
Thursday, 9 November 2017
Sunday, 12 June 2016
Does your unsubscribe work?
I have been receiving spam email, lets face it who doesn't?
So I tried to unsubscribe and the link didn't work it took me to the contact us page of the financial services company. On this page there was a complaint phone number which I called. This took me to a menu where the selections all related to credit card applications, so as well as not keen on your unsubscribing, they weren't keen on you complaining either. When I eventually got through to a human I asked to speak to their Data Protection Officer and was told they didn't have one! I asked about unsubscribing and they said they would take my details and pass them on (they weren't sure who to). Really!
So I tried to unsubscribe and the link didn't work it took me to the contact us page of the financial services company. On this page there was a complaint phone number which I called. This took me to a menu where the selections all related to credit card applications, so as well as not keen on your unsubscribing, they weren't keen on you complaining either. When I eventually got through to a human I asked to speak to their Data Protection Officer and was told they didn't have one! I asked about unsubscribing and they said they would take my details and pass them on (they weren't sure who to). Really!
Anyway while I was holding on for a person to answer the phone, I went
online and reported them to the ICO for spamming me, so my time wasn't
wasted ;-)
Always check that your unsubscribe function works. You don't want someone to report you to the ICO while they wait.
Make sure your staff are adequately trained and you have a named person who knows how to deal properly with the data protection queries.
Always check that your unsubscribe function works. You don't want someone to report you to the ICO while they wait.
Make sure your staff are adequately trained and you have a named person who knows how to deal properly with the data protection queries.
Sunday, 15 May 2016
Back to Basics - Collection Notices
One of the keys to collecting information in line with the Data Protection Act is to ensure that you are telling the person providing the information a few key things. Collection notices aren't properly understood and are sometimes overly complicated.
So here are the basics, a collection notice must tell the person providing their information:
Remember that regardless of whether you are registered with the ICO you have to comply with the Data Protection Act so any forms that you use for the collection of information MUST have a data collection notice on it. Without a valid collection notice you are breaking the law!
So here are the basics, a collection notice must tell the person providing their information:
(a) who the organisation collecting the information is
(b) what the information provided will be used for
(c) how the information will be stored and for how long
(d) whether the information will be shared with another organisation or organisations
The wording does not have to be formal, you can just write in plain english the information required.
Collection notices should be provided on both paper and electronic forms. Frequently individuals do not remmebr signing up for something or when they gave information so to ensure that you stay off the ICO's naughty step you should record when the information was collected and this should be retained for the life of your relationship with the individual. Additionally, if it is a paper form you either need to hold the hard copy or have a scanned copy for your records. This will all help with proving that you are protecting the individuals privacy should you need to.
The wording does not have to be formal, you can just write in plain english the information required.
Collection notices should be provided on both paper and electronic forms. Frequently individuals do not remmebr signing up for something or when they gave information so to ensure that you stay off the ICO's naughty step you should record when the information was collected and this should be retained for the life of your relationship with the individual. Additionally, if it is a paper form you either need to hold the hard copy or have a scanned copy for your records. This will all help with proving that you are protecting the individuals privacy should you need to.
Remember that regardless of whether you are registered with the ICO you have to comply with the Data Protection Act so any forms that you use for the collection of information MUST have a data collection notice on it. Without a valid collection notice you are breaking the law!
Sunday, 8 May 2016
Back to Basics - What is personal information?
There was a discussion on one of the forums that I belong to about what is considered personal information.
Personal information is any information which relates to a living individual who can be identified -
(a) from that information, or (b) from that information and other information which is in, or is likely to come into the possession of your organisation.
So if you code an account with the reference 123 and in another file link reference 123 with John Smith, then both pieces of information are considered personal information as they can then relate to a living individual.
For example a hairdresser who retains details of their clients, even something simple like a phone and contact number and dates of appointments, are retaining personal information under the Data Protection Act.
Personal information is any information which relates to a living individual who can be identified -
(a) from that information, or (b) from that information and other information which is in, or is likely to come into the possession of your organisation.
So if you code an account with the reference 123 and in another file link reference 123 with John Smith, then both pieces of information are considered personal information as they can then relate to a living individual.
For example a hairdresser who retains details of their clients, even something simple like a phone and contact number and dates of appointments, are retaining personal information under the Data Protection Act.
Monday, 2 May 2016
How many complaints before you need to take action?
I am often asked how many complaints the Information Commissioners Office (ICO) need about a company before they start to take action. There is no definitive answer. I have known companies have as few as 12 complaints raised with the ICO before they start to make enquiries into a businesses practices. It is easy for someone to complete the online form and raise a "concern" with the ICO. When the ICO starts to investigate your practices, it can take up to six months to resolve the queries raised and receive a conclusion from the ICO as to what action they intend to take against your business.
If you are working on the basis that you won't improve your information security practices until the ICO starts to take an interest, you might not have to wait long. Data Protection is becoming more high profile and, as can be seen from the bad publicity, something that is featured in the news on a regular basis. The outcome of any investigation will depend on the type of complaint, number of complaints and the personal information involved. We regularly provide support to businesses as they go through the investigation process.
What would you do?
If you are working on the basis that you won't improve your information security practices until the ICO starts to take an interest, you might not have to wait long. Data Protection is becoming more high profile and, as can be seen from the bad publicity, something that is featured in the news on a regular basis. The outcome of any investigation will depend on the type of complaint, number of complaints and the personal information involved. We regularly provide support to businesses as they go through the investigation process.
What would you do?
Sunday, 17 April 2016
Incident Trends for Data Protection Breaches
The Information Commissioners Office has published the list of ways in which personal data has been inadvertently disclosed over the last quarter. This is based on the information received by the ICO. There are undoubtedly a significant number of breaches which are never disclosed to the ICO but those that are show a definite trend.
The graph below is reproduced from the ICO website. Here's the link to the full page https://ico.org.uk/action-weve-taken/data-security-incident-trends/
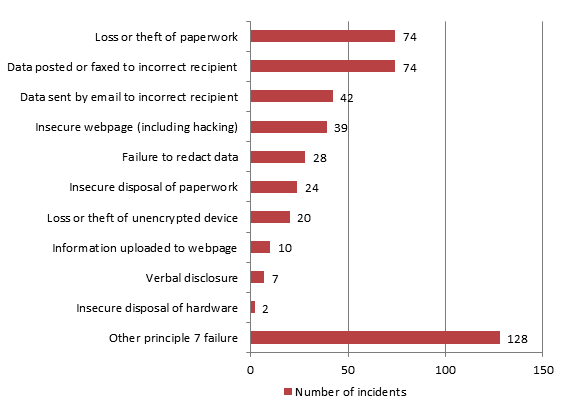
Top of the incidents reported is sending an email to the wrong person. Surprisingly this is followed by information being posted or faxed to the wrong person. In contrast, providing personal information verbally to the wrong person is quite low. Is this because we are more sceptical about providing information over the phone or in person to someone? The training provided by companies often focusses on this area and that may also be why this figure is so low.
The above list should be an indication to all organisations of the key areas where there is scope for losing personal information, so what steps do you have in place to make sure that information is not leaked or disclosed from your organisation in the same ways?
Sunday, 3 April 2016
Who is letting your organisation down?
There have been a number of high profile data breaches by members of staff in organisations.
From the disgruntled Morrison's employee who leaked the salaries of staff onto the internet and was subsequently jailed for 8 years to the Tesco employee who was emailing details of customers to his personal email account and the Enterprise car rental employee who was selling customer information to a claims company, the main weaknesses in most organisations are the staff.
So what do you do about it? The cases shown above have been high profile and widely reported but organisations are probably suffering breaches on a regular basis and may not even be aware of them. We get used to what we see and do and so often we forgot to stand back and view the situation with fresh eyes.
When I start to work with organisations, I am that fresh pair of eyes. I often also represent your clients. Are you collecting information to help you communicate effectively with them? We can easily identify the areas in your business where there is potential for losing your business information.
If you want to find out more, we offer a free initial consultation so you can see how we would work with you. Contact us today to book a meeting.
From the disgruntled Morrison's employee who leaked the salaries of staff onto the internet and was subsequently jailed for 8 years to the Tesco employee who was emailing details of customers to his personal email account and the Enterprise car rental employee who was selling customer information to a claims company, the main weaknesses in most organisations are the staff.
So what do you do about it? The cases shown above have been high profile and widely reported but organisations are probably suffering breaches on a regular basis and may not even be aware of them. We get used to what we see and do and so often we forgot to stand back and view the situation with fresh eyes.
When I start to work with organisations, I am that fresh pair of eyes. I often also represent your clients. Are you collecting information to help you communicate effectively with them? We can easily identify the areas in your business where there is potential for losing your business information.
If you want to find out more, we offer a free initial consultation so you can see how we would work with you. Contact us today to book a meeting.
Sunday, 20 March 2016
The unencrypted hard drive - missing from a prison…
The Information Commissioner’s Office really had no choice
but to come down hard on the National Offender Management Service recently,
after a portable hard drive used to back up the prisoner intelligence database
went missing from a prison security department.
Although nobody knew when it had actually gone missing, it
could have been gone for almost a week since it had last been used on 18 May
2013 for the weekly back up - but was missing when staff went to back up six
days later. It had not been locked in the fireproof safe afterwards, contrary
to policy. Not only was it missing, it
was also unencrypted and had not been password protected. It contained
sensitive information about almost 3000 prisoners, including names and dates of
birth, length of sentence, offence(s), physical descriptions and distinguishing
marks, plus intelligence information about drug use and links to other
prisoners or organised crime - certainly not the sort of details you’d want to
lose.
Although only nine staff members had access to the area
where the hard drive was used and the area was controlled by a keypad system,
the door to the Security Department could be opened by anyone on the prison
staff.
To make matters worse, this wasn’t the first time something
like this had happened. Back in October 2011, an almost identical breach
involving 16,000 prisoners in another establishment had taken place, and the
ICO had been told that because of this, encrypted hard drives had been supplied
to 75 prisons that had been using unencrypted portable hard drives to back up prisoner
intelligence information. Unfortunately, nobody realised that the encryption
software required manual activation and the IT provider was never asked to
check that the encryption software was working, so all the 75 prisons carried
on using insecure portable hard drives for at least a year afterwards.
The software has now been activated and automatic upgrades
enabled. The hard drive was never recovered although it doesn’t appear to have
been accessed and there was no evidence that it fell into the wrong hands.
Because there had already been a virtually identical serious
breach, the Commissioner considered that this was a very serious contravention
of the seventh data protection principle;
“Appropriate technical
and organisational measures shall be taken against unauthorised or unlawful
processing of personal data and against accidental loss or destruction of, or
damage to, personal data”
The National Offender Management Service was fined £180,000.
It just underlines the fact that even though you think you’re doing everything
you can to comply with the rules, sometimes it can be the simplest thing you
overlook that can lead to a damaging security breach.
Do you know where your backup drives are kept, and have
official policies in place to ensure that they don’t go missing? Are the drives encrypted? Can you
imagine what would happen if the personal information you keep backed up were
to be lost, either for your business or your clients? If you’re unsure of how
to make sure that this sort of faux pas doesn’t ever happen to you, contact me
and I will be delighted to provide you with guidance and advice.
Sunday, 13 March 2016
Why hire a Data Protection Specialist?
When I am out networking, one of the questions I frequently get asked is "why do I need to hire a data protection specialist?".
There are lots of skills that an organisation is happy to buy in because they recognise that there is a need for specialist knowledge. You would always ask for legal advice when entering into a contract or lease, you obtain insurance advice as to the level of cover you require and the type of insurance that best suits your business, when implementing a new software package you would seek the advice of the software developers to ensure it meets your needs. So what stops you seeking qualified advice for your data protection compliance?
The Data Protection Law is a complex piece of legislation and has been around for about 18 years; additionally over the years good practice guides and enhancements have been made. I have been a Data Protection Officer for about 12 years and I have studied for and gained the qualification to show that I have the skills and knowledge to provide advice to organisations.
There is lots of advice on the Information Commissioners Website (the regulator for data protection in the UK) and you can find out the basics there. If your business is complex, has more than 25 employees or holds personal information about an individuals health, well-being or criminal convictions, then you really need to get specialist advice.
A data protection specialist, like me, will look at your organisation and the information you are collecting and holding. They'll also provide tailored advice to protect the information you hold and also help you identify how to use it more efficiently. The requirements of the Data Protection Act should not be onerous as they are based on good practice for information security.
The cost of getting advice is likely be far less than any monetary cost that your organisation might suffer as a result of the loss of information, either through accidental or malicious means.
If you want to have a discussion with me about your organisation and how we can help, we offer a free initial discussion so contact us to see how we can help improve your use of the information you collect.
There are lots of skills that an organisation is happy to buy in because they recognise that there is a need for specialist knowledge. You would always ask for legal advice when entering into a contract or lease, you obtain insurance advice as to the level of cover you require and the type of insurance that best suits your business, when implementing a new software package you would seek the advice of the software developers to ensure it meets your needs. So what stops you seeking qualified advice for your data protection compliance?
The Data Protection Law is a complex piece of legislation and has been around for about 18 years; additionally over the years good practice guides and enhancements have been made. I have been a Data Protection Officer for about 12 years and I have studied for and gained the qualification to show that I have the skills and knowledge to provide advice to organisations.
There is lots of advice on the Information Commissioners Website (the regulator for data protection in the UK) and you can find out the basics there. If your business is complex, has more than 25 employees or holds personal information about an individuals health, well-being or criminal convictions, then you really need to get specialist advice.
A data protection specialist, like me, will look at your organisation and the information you are collecting and holding. They'll also provide tailored advice to protect the information you hold and also help you identify how to use it more efficiently. The requirements of the Data Protection Act should not be onerous as they are based on good practice for information security.
The cost of getting advice is likely be far less than any monetary cost that your organisation might suffer as a result of the loss of information, either through accidental or malicious means.
If you want to have a discussion with me about your organisation and how we can help, we offer a free initial discussion so contact us to see how we can help improve your use of the information you collect.
Sunday, 6 March 2016
Put on your dancing shoes - or not!
I have been receiving emails about dance classes for the last few months, I don't remember signing up for them and anyone who knows me will testify to the fact that I have no sense of rhythm at all.
Anyway, somehow I have been added to this mailing list for dance classes. I started receiving emails about three months ago and on average I get three a week. On occasion I have had two a day. There is no method to unsubscribe from the emails. Having got bored with receiving the emails I decided to respond to an email by asking to be removed from the mailing list. I did this on two occasions a week apart. I didn't receive a reply. The other day another email pinged into my email inbox and I decided I needed to take direct action so I rang the telephone number shown. It went to an answerphone giving me details of the classes available (Was there no escape?).
I decided I would call back again later. Just after I put the phone down, a text came in - guess what - it was a text to tell me about dance classes from the number I had just called. I was furious. I rang the number again, this time it was answered. I explained that I was very angry that I was receiving these emails and to receive a text was just too much - I had not given her permission to send me marketing by text message. The response - "Well people call me all the time wanting to know the times of dance classes so I don't answer the phone and send them a text" - really, you don't think that sending emails and the answer phone message giving information about dance classes is enough, you decide to send spam texts as well. "Nobody else has complained" (that old chestnut).
I asked about the previous emails asking to be unsubscribed and she told me she hadn't received them. I asked her to remove me from her mailing list, so I gave her my email address and she searched, only to tell me it wasn't there. I said it must be, you are sending me three emails a week on average. "Oh no that isn't possible as that would mean you were on three lists". She rechecks and finds I am on her database and on three lists (big surprise!). She said she had been hacked about a month ago and the hacker must have put me on the lists (so a hacker breaks into her email account and adds my name to three of her mailing lists so she can send me emails about dance classes, what a helpful hacker!). She tells me she cannot delete me from her database, "it won't let me". I reinforce the fact I wish to be removed from the mailing lists and how she does it is not my problem, I say goodbye and hang up. A little while later another email comes in from her to tell me she has removed me from her mailing lists but she had to remove 10 other people to be able to do it.
 What did I learn?
What did I learn?
- the dance class provider is not registered with the ICO - potentially a £5k fine and criminal record from not being registered.
- the emails she is sending breach PECR (Privacy and Electronic Communication Regulations) by not having a means to easily unsubscribe.
- Failing to remove me from her mailing list on the two previous occasions is another PECR breach.
- Sending me an unsolicited marketing text is a data protection breach - The ICO has recently fined a company £200k for unsolicited marketing texts.
- the most important thing to her was using the personal information she had gathered to further the spread of her message and the need for security and professionalism that comes from having a client list was lost on her.
If I was advising her, what should she be doing?
- Register with the ICO - a £35 annual fee
- Use a proper mailing package such as mailchimp, madmimi, constant contact etc so that she can properly manage her mailing list and those people who are desperate to unsubscribe can do so without the hassle I had.
- a proper mailing package would also be less likely to be hacked, providing she has a decent security password.
- Stop sending texts to people automatically, she is potentially raising the risk of the ICO investigating her. To be able to send marketing texts you have to have the specific permission of the individual.
- Think about the security of the information she is holding. Would she be happy with her personal information being dealt with in this way?
This is the worst case of failing to find out the requirements for running a business with a marketing list that I have come across in a while, that is unless you know better. Let me know.
Anyway, somehow I have been added to this mailing list for dance classes. I started receiving emails about three months ago and on average I get three a week. On occasion I have had two a day. There is no method to unsubscribe from the emails. Having got bored with receiving the emails I decided to respond to an email by asking to be removed from the mailing list. I did this on two occasions a week apart. I didn't receive a reply. The other day another email pinged into my email inbox and I decided I needed to take direct action so I rang the telephone number shown. It went to an answerphone giving me details of the classes available (Was there no escape?).
I decided I would call back again later. Just after I put the phone down, a text came in - guess what - it was a text to tell me about dance classes from the number I had just called. I was furious. I rang the number again, this time it was answered. I explained that I was very angry that I was receiving these emails and to receive a text was just too much - I had not given her permission to send me marketing by text message. The response - "Well people call me all the time wanting to know the times of dance classes so I don't answer the phone and send them a text" - really, you don't think that sending emails and the answer phone message giving information about dance classes is enough, you decide to send spam texts as well. "Nobody else has complained" (that old chestnut).
I asked about the previous emails asking to be unsubscribed and she told me she hadn't received them. I asked her to remove me from her mailing list, so I gave her my email address and she searched, only to tell me it wasn't there. I said it must be, you are sending me three emails a week on average. "Oh no that isn't possible as that would mean you were on three lists". She rechecks and finds I am on her database and on three lists (big surprise!). She said she had been hacked about a month ago and the hacker must have put me on the lists (so a hacker breaks into her email account and adds my name to three of her mailing lists so she can send me emails about dance classes, what a helpful hacker!). She tells me she cannot delete me from her database, "it won't let me". I reinforce the fact I wish to be removed from the mailing lists and how she does it is not my problem, I say goodbye and hang up. A little while later another email comes in from her to tell me she has removed me from her mailing lists but she had to remove 10 other people to be able to do it.
 What did I learn?
What did I learn?- the dance class provider is not registered with the ICO - potentially a £5k fine and criminal record from not being registered.
- the emails she is sending breach PECR (Privacy and Electronic Communication Regulations) by not having a means to easily unsubscribe.
- Failing to remove me from her mailing list on the two previous occasions is another PECR breach.
- Sending me an unsolicited marketing text is a data protection breach - The ICO has recently fined a company £200k for unsolicited marketing texts.
- the most important thing to her was using the personal information she had gathered to further the spread of her message and the need for security and professionalism that comes from having a client list was lost on her.
If I was advising her, what should she be doing?
- Register with the ICO - a £35 annual fee
- Use a proper mailing package such as mailchimp, madmimi, constant contact etc so that she can properly manage her mailing list and those people who are desperate to unsubscribe can do so without the hassle I had.
- a proper mailing package would also be less likely to be hacked, providing she has a decent security password.
- Stop sending texts to people automatically, she is potentially raising the risk of the ICO investigating her. To be able to send marketing texts you have to have the specific permission of the individual.
- Think about the security of the information she is holding. Would she be happy with her personal information being dealt with in this way?
This is the worst case of failing to find out the requirements for running a business with a marketing list that I have come across in a while, that is unless you know better. Let me know.
Sunday, 28 February 2016
Bring your own device - and don’t lose data
Working from home and being able to take work out of the
office makes working life easier but can be a nightmare for data privacy. With
an estimated 56 per cent of employees reporting that they either very frequently
or frequently stored sensitive data on their laptops, smartphones, tablets, and
other mobile devices, the chances of confidential information getting lost or
into the wrong hands are very high.
 Bring-Your-Own-Device (BYOD) is part of the modern workplace. It’s becoming more and more normal for business information to be stored in
or accessed by devices that are not fully controlled by IT administrators, and
the possibility of data breaches caused by personal devices that aren’t
properly protected is also on the rise.
Bring-Your-Own-Device (BYOD) is part of the modern workplace. It’s becoming more and more normal for business information to be stored in
or accessed by devices that are not fully controlled by IT administrators, and
the possibility of data breaches caused by personal devices that aren’t
properly protected is also on the rise.
Protecting business information on mobile devices can be as simple as
encrypting files and/or password protecting the device - it won’t stop them
being lost but IT admin will be able to selectively remove sensitive encrypted
data and the chances of someone using stolen information maliciously are
much smaller if it’s not possible to get straight into any files that may be
sensitive. The issue is clouded when the device actually belongs to the
employee and not the business, however.
Most businesses think nothing of allowing employees to use
their own devices to access email, office calendars and contacts, and a
strong BYOD policy is vital if company information is accessible on the go, via
personal devices.
Which devices are allowed?
It’s up to you to set the boundaries and specify what’s
acceptable. If you only want to support employees’ personal Android devices and
not iPhones or iPads, or vice versa, make that policy and stick to it.
Enforce strict security rules
People don’t like having complicated passwords and lock
screens - they get in the way of fast access to their devices and longer, more
effective passwords are also easier to forget. If they are using their own
mobile devices for work however, you can’t afford to leave them on a swipe and
go setting. If your staff members want to be able to use their own gadgets for
work too, they will just have to accept that they need to use a complex
password to access them.
Banning apps
This also applies to corporate devices - social media
browsing apps, email applications and VPNs or other remote-access software need
careful consideration when you’re formulating a data protection policy.
Although the devices are people’s own, they will have to consider business
needs if they want the convenience of using them for work, and that includes
not using apps or settings that could potentially compromise data security.
Businesses also need to consider what could happen if an
employee leaves the company - you will have to have an agreed policy in place
allowing you to remove any access tokens, e-mail, data and other access
permissions.
Does your organisation have a BYOD policy? Do you have
permission from your employees to delete information from their personal devices
remotely when they leave, or if it’s lost/stolen? What safeguards are in place
to ensure that staff don’t store sensitive information remotely? If you need
advice on setting BYOD policies that keep your sensitive data safe, contact me
and I will be delighted to provide you with guidance and advice.
Sunday, 21 February 2016
9 cybersecurity fixes for businesses on a budget
For small businesses, a data breach can be expensive - it
could even cost you your business. According to some studies, it’s been
estimated that around half of companies are forced out of business within six
months of a cyber breach.
One unfortunate trend that’s being picked up is that smaller
businesses are increasingly becoming the targets of cybercrime - it’s not just
major companies that are being held to ransom by hackers. It doesn’t help that
a lot of smaller businesses rely on third-party services and growing amounts of
computer equipment, both of which leave them ever more open to the threat of an
attack.
It’s the big companies that make all the headlines, but this
can be a factor in lulling smaller businesses into a false sense of security
when in fact they are most at risk - more than 80 per cent of breaches are
estimated to happen to small businesses. But with limited resources, how can
you effectively secure your business against cyber threats?
Some of the solutions are obvious; for example 90 per cent
of attacks can be avoided if a company uses basic measures such as firewalls,
default passwords, VPNs and double authentication. In addition, there are a few extra quick
security fixes you can easily put in place to make sure everyone in the
business does their bit to avoid a potentially devastating security breach.
1. Update your PC
Out of date software may not be supported or updated,
leaving it open to threat. If you have any computers still running Windows XP,
for example, get them upgraded - support and updates for Windows XP haven’t
been available since last year!
2. Train your staff
Have a clear data protection policy in place and make sure
everyone is clear about what they can and cannot store on their personal
computers.
3. Keep sensitive data protected
Don’t use the same computer for storing sensitive data that
you use for checking office email or surfing the web, keep a dedicated machine
just for that purpose.
4. Review your stored information
Review the information that’s stored on your server(s) on a
regular basis and make sure that confidential or financial data is properly
protected.
5. Keep PCs well protected
Check that all your office PCs, laptops and tablets have
automatic software and antivirus updates enabled and keep firewalls switched
on.
6. Plan ahead
Put together a backup plan, which includes things such as who
you need to call to arrange offsite backup if the worst happens, whether it’s
hackers, a fire or flood, or physical theft of equipment. Keep a record of
insurance policy details and what policies actually cover.
7. Do your homework
Keep a close eye on computer logs and occasionally review
them as they will prove valuable during an incident. Well maintained logs help
you to understand what your computers normally do, which could help you spot hackers
before they cause any damage.
8. Consider using a managed security service
Managed security services give you an extra layer of
protection, and peace of mind that your business is as well-protected as a
larger firm.
9. Support knowledge sharing
If we all share our actionable data on cyber breaches, it
means that experts get an update on shared threats that exist. Knowing what’s
out there gives the experts the opportunity to come up with an analytic
approach to reflect the risk of cyber threats.
Do you have a security policy in place? If you’re unsure of
how to protect your data, contact me and I will be delighted to provide you
with guidance and advice.
Subscribe to:
Posts (Atom)
